Control Advantage
- cloud platforms controls almost every aspect of their users' lives
Private Cyberspace turns the existing Cloud Control Flow UPSIDE DOWN, by letting the user control application through infrastructure.
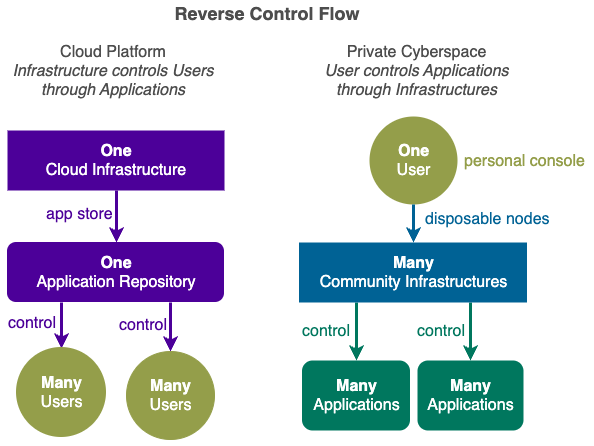
Private Cyberspace turns the existing Cloud Control Flow UPSIDE DOWN, by letting the user control application through infrastructure.

Making Private Cyberspace affordable and attractive to all 8 billion on earth requires a PARADIGM SHIFT in economies of scale:
Private Cyberspace removes the COST barrier to RELIABLE infrastructure by leveraging community idle capacities (e.g. unused disks, bored retirees), reusing broken devices (e.g. laptops with faulty screens & keyboards) and taking over data income from the Cloud.
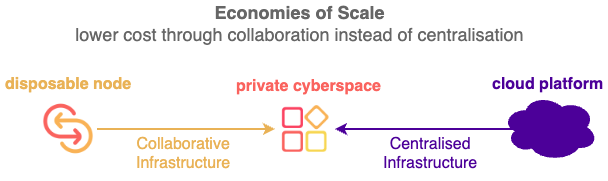
Currently most people can only collaborate via cloud platforms, with private cyberspace everyone can collaborate directly and benefit from network effects that were only available cloud platforms before.
Digital Equity
Private Cyberspace removes the COST barrier by leveraging community idle capacities (e.g. unused disks, bored retirees), reusing broken devices (e.g. laptops with faulty screens & keyboards) and taking over data income from the Cloud.
Private Cyberspace removes the COST barrier to private cyberspace ownership by aggregating surplus resources from others and taking over data income from the Cloud. Everyone now have RELIABLE infrastructure to operate at any scale, no matter their wealth.
A major dilemma with selling your data is the lack of privacy, the more data you sell the less privacy you have. So your data income was essentially limited by how much privacy you are willing to lose.
Private Dataspace solves this income dilemma by letting you sell your data without losing your privacy with the world's first deployment of homomorphic encryption at population scale.
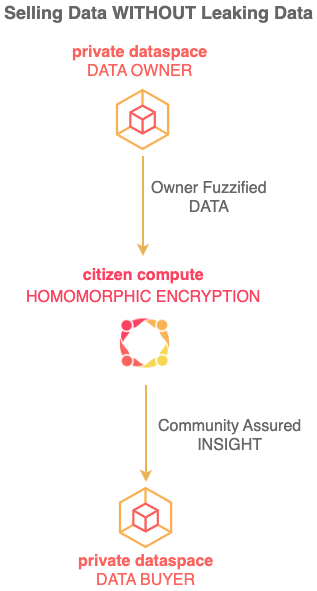
Private Dataspace uses a novel 2 step data exchange process to not just protect owner privacy but also to ensure maximum return on owner data.
If someone uses your personal data and infrastructure built with your tax dollars to generate massive profits from their AI models, may be they should give you some money in return ?
Instead of money, now that you have you own Private Cyberspace with compute power, may be they can:
Once you have collected some data into your own private cyberspace, you can OPTIONALLY work other cyberspaces in a safe and synergistic manner to solve the most difficult problems facing humankind.
For example, currently you can earn bronze y20coins anonymously (e.g. for helping to locate COVID virus down to meters and cut its legs off within minutes by notifying others).
From the wifi signals on the street to the barcodes on a bottle of milk, you can donate or sell the the data you have collected in your Private Cyberspace immediately on collection or on a later date.
Selling DATA in your Private Cyberspace redirects the funds originally going to the Cloud Platforms to you, however Private Cyberspace also let you sell INSIGHTS by processing your data yourself and then selling the resulting insight, which is substantially safer than exposing your data to others.
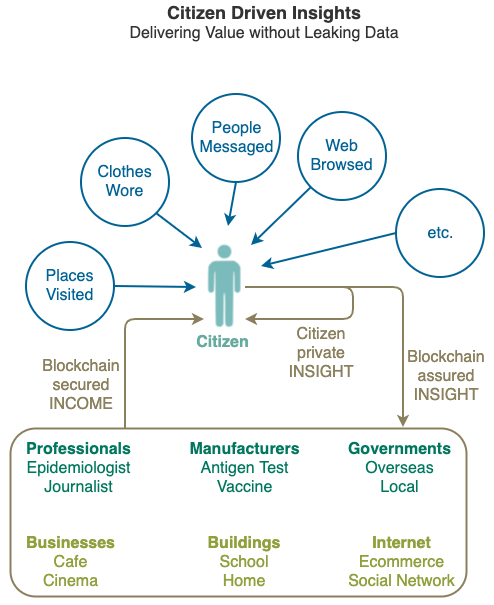
You can also use your Private Cyberspace to receive data anonymously, from a pothole on the road in front to an active shooter in the building, from an ambulance coming up behind you to proving you are somewhere else at a certain time in courts ... the possibilities are endless.
Innovation sets Human Intelligence apart from Artificial Intelligence, innovation needs compute and data to thrive, restricting the compute and data to dozens of companies worldwide is directly restricting the ability of the rest of us to innovate.
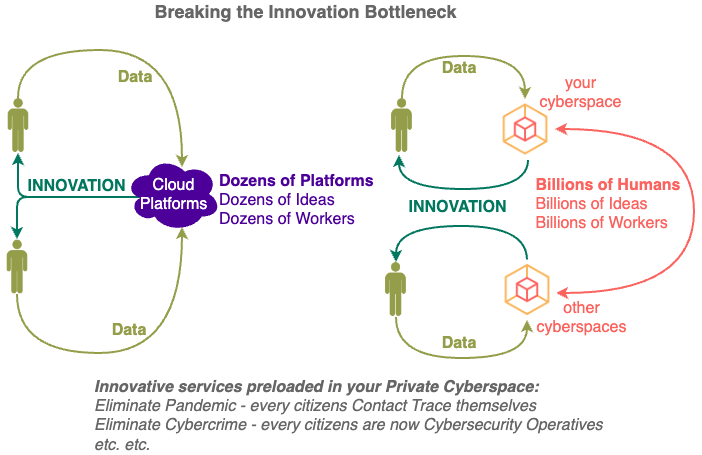
No matter how smart the staff are at the Cloud Platforms (Apple, Google, Open AI etc.), the diversity introduced through the participation of the rest of the world will result in MORE and BETTER innovations.
Most importantly, those innovations will be carried out under the DIRECTIONS of billions of citizens instead of dozens of board members.
Private Cyberspace provides instant compute power to MANY so their digital lives are no longer dependent on the compute power from a FEW (e.g. Apple, Google, ChatGPT etc.).
analysing detailed data deeply (previously not possible on cloud platforms due to privacy reasons)
interacting directly with people safely (previously you need to go through cloud platforms)
Each person can have one or more Private Cyberspaces and each Private Cyberspace can operate under one or more aliases.
Unlike Cloud Platforms which attempt to identify you and target you even across applications and sites, Private Cyberspace encourages you to have different identities for different purposes. Fine grain control allows you to tune each alias for different groups of people and different types of applications.
New Private Cyberspaces always start operation with a PRIVATE alias - there is NO identity information and NO data leaves your phone - you can even collect data OFFLINE. You can confirm that feature by continuing to collect data after you have disabled all communication functions e.g. turn on "air plane mode" of your phone. Programmers can confirm by auditing the javascript code already loaded in your browsers.
PRIVATE alias is used to collect raw data privately on your phone and sharing them at your own time and through your own means, there is no interaction with any exchange. In fact, since the Console will not "phone home" to application providers under GUEST alias, you will need to check for new software updates manually, it will not check itself. Basically you are using the Console to built your information assets "off the grid".
GUEST aliases are used for interacting anonymously with exchanges. You will start to see more information (like the name of the local government area you are currently in) and be able to.
Private Cyberspace enables you to EXCHANGE surplus compute power with others in the community e.g. use the others' laptops when they are asleep or backup your data to the unused capacities on their hard disks.
Private Cyberspace enables you to purchase compute power using the data income from the information ASSET you have collected e.g. external data like WiFi signal strengths on the street or personal data like the barcode on the drink you purchased.
Private Cyberspace's barrier to entry for people without a smart phone is approximately AU$39 (WiFi is sufficient no need for mobile SIM), making a nationwide Virtual Vaccine program substantially cheaper than the never ending costs to taxpayers of real vaccines.
Consumer enhanced Productivity adds ability for each consumer to on top of traditional Producer driven Productivity e.g. get rewarded for useful comments you made on public forums, earn from idle bandwidth and unused disk spaces while you sleep.
Australian Government Productivity Submission
Private Cyberspace can take advantage of the abundant compute provide by Citizen Synergy to fight cybercrime - every owner is now a cybersecurity operative.
When a single organisation has control of all your data, it does not matter how much it claims it has done to protect your privacy and security (e.g. uses open sourced software, does not keep logs on servers etc.).
Take the Signal service as an example, which is endorsed by Edward Snowden and Elon Musk:
We are talking about ONE party getting ALL the phone numbers, ALL the times of call connection, ALL IP addresses of ALL its users worldwide (as well as leaking metadata to Apple and Google).
Signal is just an example, these trust problems apply to ANY centralised service that claims to protect "privacy" e.g. your favourite VPN Service or Bitcoin Mixer. And if they ask for payment, which any proper service should, then you just created another attack vector into your identity.
The problem does not only apply to niche small companies that aggregates data, what about the biggest Single Vendor there is, Apple ?
Has Apple ever inform you or asked for your permission before starting to use your phone, your internet bandwidth, your battery power, your person location to help them sell more Air Tags ?
The trust problems above also apply to all devices which are connected to the internet from cameras to teddy bears and of course mobile phones.
Whether it is remote servers in the cloud or the mobile phone in your hand, centralising data on devices that you have little control is dangerous. From iOS hacks to Android vulnerabilities to methods leaked in Vault 7 the data centralised on the mobile platform are too valuable to be left alone.
Large centralised databases (storing your location, contacts etc.) become very high value targets, look at the massive leaks at Facebook which just happened AGAIN after the problem was supposed to have been fixed after the last leak.
Citizen Computing has been designed assuming that Nodes will get hacked, that Nodes will be lost, that Nodes will be located with people who turned "bad" etc., so by cutting up an Application into as many Nodes as possible. More importantly you can change the number of Nodes, for some Applications you might want additional Nodes to be extra safe.
There are separations between Zones (e.g. Personal, Fiduciary, Community etc.), there are separations between functions (e.g. Identification, Collection, Distribution, Notification etc.), there are separations based on time (e.g. maximum one day's data), there are separations of networking, processing, storage and the physical location site itself (so they can all keep an eye on each other).
The less amount of data a Node holds, the less data there is to be stolen if that node got hacked and the easier it is to recover if that Node got damaged.
The more Nodes you have, the less damage can be done by one and the more they can check on each other.
Citizen Computing lets you specify which Node to use for which Module, so for some Modules you might like to use Nodes from people you actually know and located in places you have actually visited.
7. Universal Encryption
With Citizen Computing everything is encrypted whenever possible, double or even triple in most cases.
8. Aliases Encouraged
People need to behave differently in front of different groups of people, you need them to know different things about you.
Getting everyone you know on the SAME "social" platform to see one view of you or timeline of yours just does NOT make sense!
For different situations, Citizen Computing allows you to disclose different and just enough information about yourself under each identity, leaving out the rest of the data for privacy and profit.
9. Independent Monitoring
Citizen Computing has basic security rules which prevent you doing dangerous things in general (e.g. uploading unencrypted data to Nodes outside of your Personal Zone, blocking known bad IP addresses etc.) all of which you can of course turn off.
A fundamental problem with Cloud security that is impossible to fix is the lack of physical security
Protection get A LOT easier if you don't have to protect your data physically - from the owner of the computer it is on or from the owner of the room it is in - from the Cloud Platforms.
fact that you are putting your data on their computers without encryption
Cybercrimes are causing substantial damages to many individuals and organisations EVERYDAY.
Private Cyberspace mitigates System and Human Vulnerabilities by enabling citizens to block transactions INDEPENDENTLY with their own Private Cyberspaces.
It brings together the compute and data from millions of citizen devices to verify transactions even before illegitimate transactions reach affected systems.
Cloud Platforms have started to introduce Virtual Machines (VMs) secured by hardware, giving the impression that your data is secure with them.
Google promotes its Confidential Computing services confidently but the AMD SEV technology it is based on has been shown to be insecure:
Microsoft's Confidential Computing based on Intel SGX does not flair much better:
Despite the impressive sounding concept of using hardware for protection, dynamic and complex systems are always going to have weaknesses, Private Cyberspace complements Hardware Secured VMs with an independent Citizen driven Security layer.