Introduction
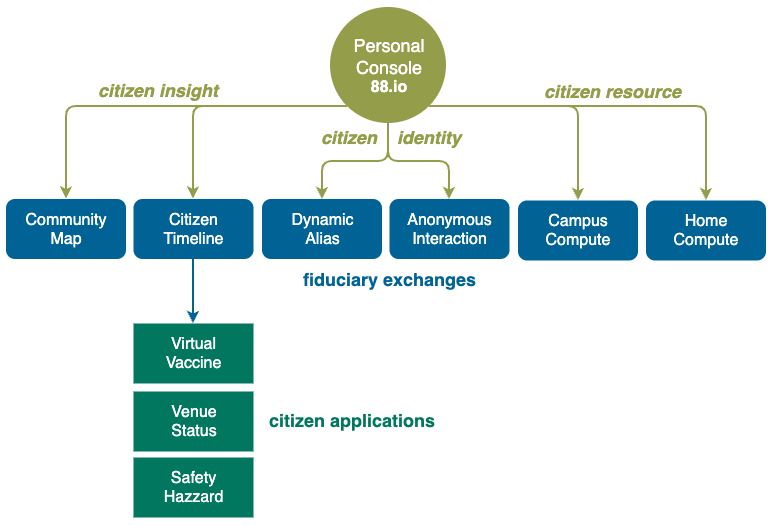
Personal Console enables non-technical individuals to own and shape their digital environments independently by simply mixing and matching compute modules. Not everyone knows how to cook, but everyone knows what tastes good.
Private Cyberspace gives you exclusive CONTROL of your information space (e.g. create aliases for different situations, define your own transactions, train your personal AI, expand your income mix etc.). Start creating value and building asset using your phone within just ONE SECOND.
Private Cyberspace make it affordable for you to import compute to process your data instead of having to export your data to cloud platforms for processing, by enabling you to leverage the latent processing power of thousands of community computers worldwide from the comfort of your personal phone.
Become an OWNER instead of user of the latest applications (AI, blockchain etc.).
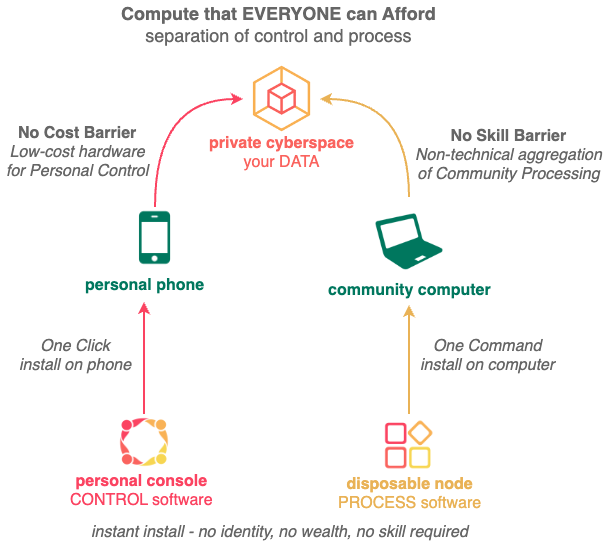
This separation of CONTROL (using Private Cyberspace software on personal phone) from PROCESS (using Disposable Node software on community computers) is a paradigm shift from traditional monolithic computing where everything is done centrally on Cloud Platforms.
1.1. Private Cyberspace Installation
With just ONE CLICK anyone can install the Private Cyberspace software into their web browsers instantly.
- NO download from App Stores or Play Store
- NO sign-up to any service or create any account
- NO contacts e.g. username, email, phone number etc. needed
- NO advertisement or any unsolicited interruption
- NO leaking of data outside of your phone
- NO charge for use, distribution, modification (refer to license)
- NO hidden operation (source code is published publicly)
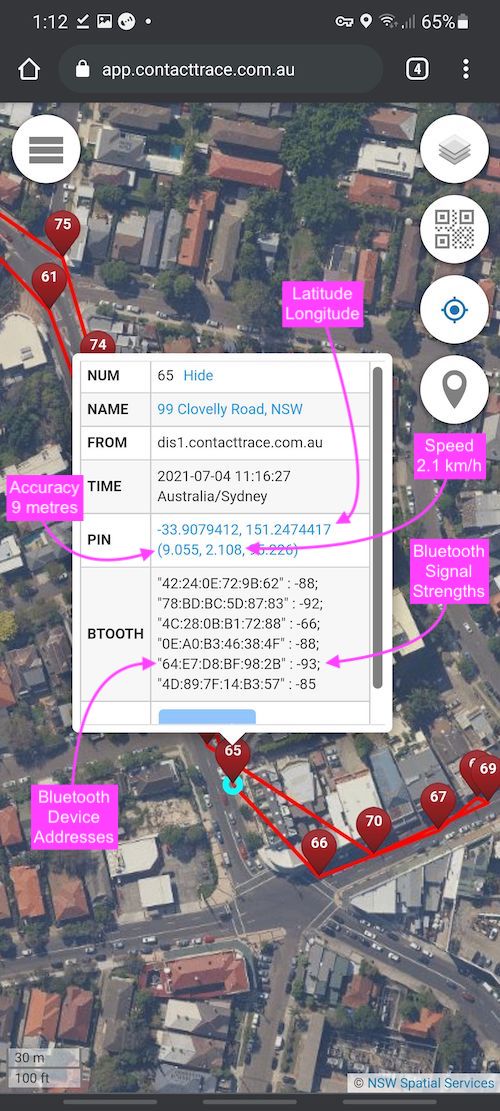
With Private Cyberspace's one click install, you will be direct the Application Integrator closest to you. For example, if you are in New South Wales, Australia your browser could be directed to install from app.contacttrace.com.au (Contact Trace Australia) which specialises in supporting the New South Wales Australia region.
Normally there are different Application Integrators covering different government regions in the world. If there is no Application Integrators in your region, you are welcome to start one yourself or use any Application Integrator you like from other regions.
After installation, you can create your first piece of Information Asset in your Private Cyberspace by following the One Second Collect tutorial in the Quick Start Guide.
- Private Cyberspace Introduction
- Private Cyberspace Quick Start
- Private Cyberspace User Guide
To maintain Private Cyberspace's security model, you MUST only run the Private Cyberspace software on personal devices that you own - hardware that you have EXCLUSIVE and FULL control of.
1.2. Console Security
To maintain Private Cyberspace's security model, you MUST:
-
Run the Private Cyberspace software on personal devices that you own - hardware that you have EXCLUSIVE and FULL control of.
-
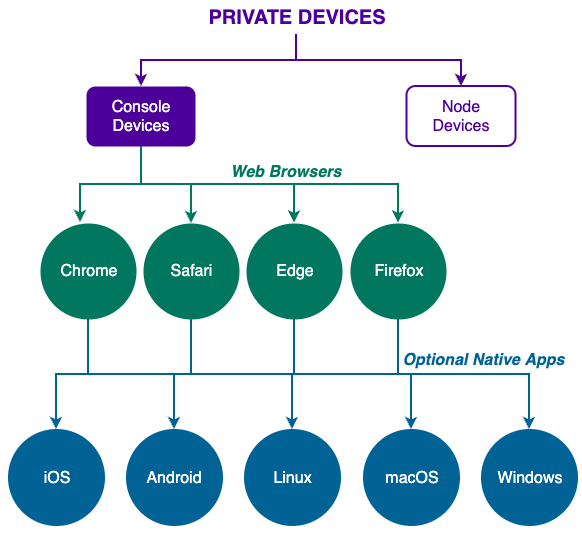
Dedicate a web browser just for Private Cyberspace (e.g. Chrome on Android and Safari on iOS) and use a different web browser (e.g. Firefox, Edge etc.) for visiting your other web sites.
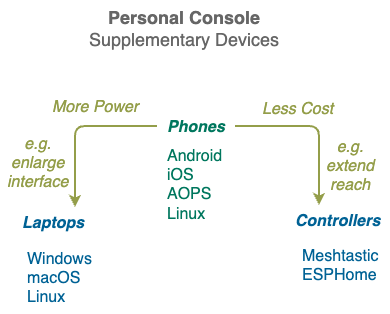
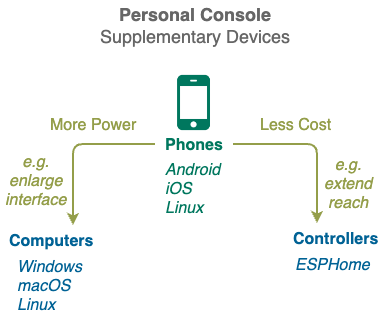
Supplementary Devices
Once the Private Cyberspace software has been installed on your phone, you can optionally add more personal devices to it to improve your Private Cyberspace experience.