Take Ownership of your Data
EVERYONE (from refugees to billionaires) can transform their data into digital ASSETS within ONE SECOND to fund their private cyberspace and regain income taken by cloud platforms.
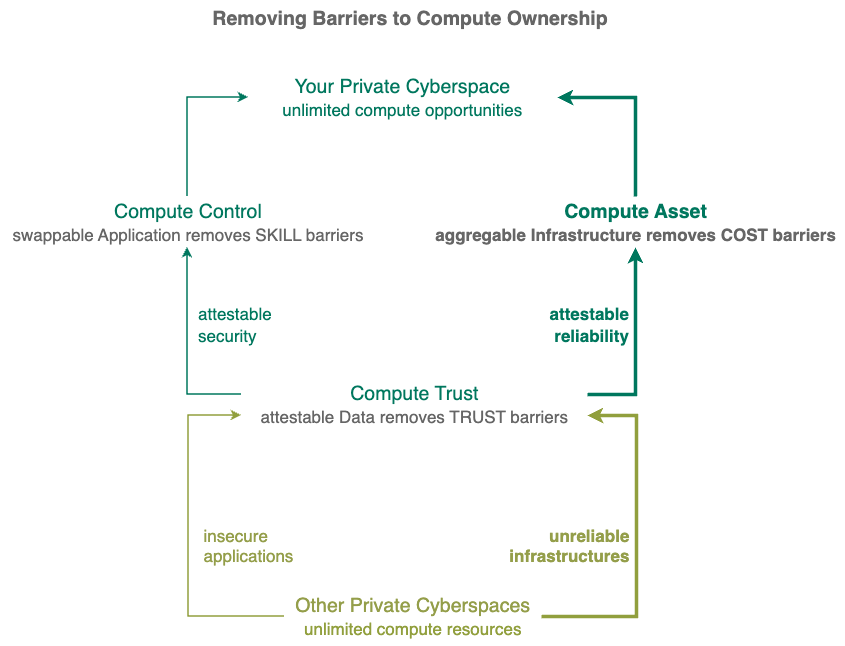
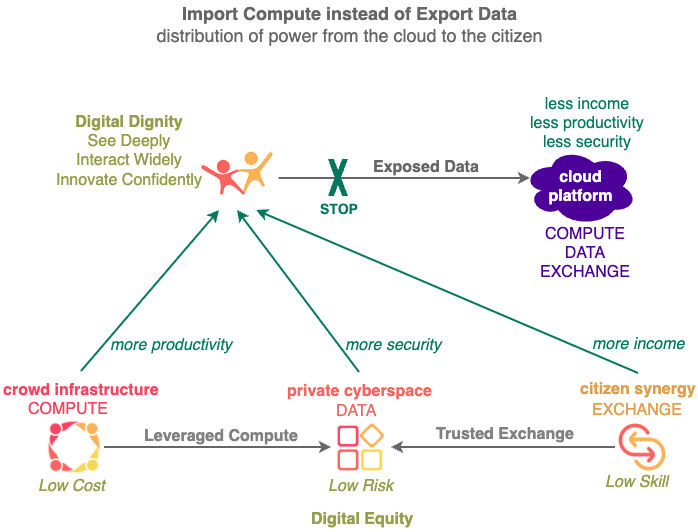
Private Cyberspace eliminates your infrastructure costs with collaborative assets. No more paying for the use of cloud infrastructure and exchange assets with others to earn extra income.
Private Cyberspace adds an independent layer of collaborative reliability around your infrastructures letting you innovate cheaply with latent resources worldwide in a RELIABLE and PROFITABLE manner without cloud platforms limitations.
Reliability Layer around all your infrastructures, leveraging latent resources worldwide (unused storage, bored retirees etc.) to provide the REDUNDANCY and SCALABILITY needed to achieve sustained population scale effects.
EARN INCOME from your data without cloud platforms, leverage latent resources worldwide
Earn income from your private cyberspace outside the restrictions of , collaborate freely
Fund your Start transferring profits from your data cloud platforms back to yourself,
1. Collaborative Compute
Community Cluster facilitates easy aggregation of unreliable infrastructures. Evolve from a passive user to an active OWNER of infrastructure. Leverage latent resources worldwide , gain Privacy, Scalability, Reliability not possible on Cloud Infrastructures.
Be an OWNER instead a user of latest technologies from AI to blockchain, aggregate the compute and data on billions of devices to solve intractable problems have defeated even the most powerful nations.
Take advantage of lates latent infrastructure worldwide
Remove skill and cost barriers to infrastructure
Reduce waste, prevent fraud, break monopoly that are traditionally
use Citizen Synergy to leverage global latent infrastructures cheaply, from the comfort of your home.
Transfer compute power from centralised Cloud Platforms to collaborative Community Clusters easily using YOUR PHONE. No matter your wealth or skill levels - leverage worldwide resources to solve intractable problems with COLLABORATIVE COMPUTE.
1.1. Why Community Cluster ?
Why Community Cluster ?
Collaborative Compute
Community Cluster enables everyone, from billionaires to refugees, to store their DATA and receive all the COMPUTE power they need to build up their own information assets, independent of their wealth or skill levels.
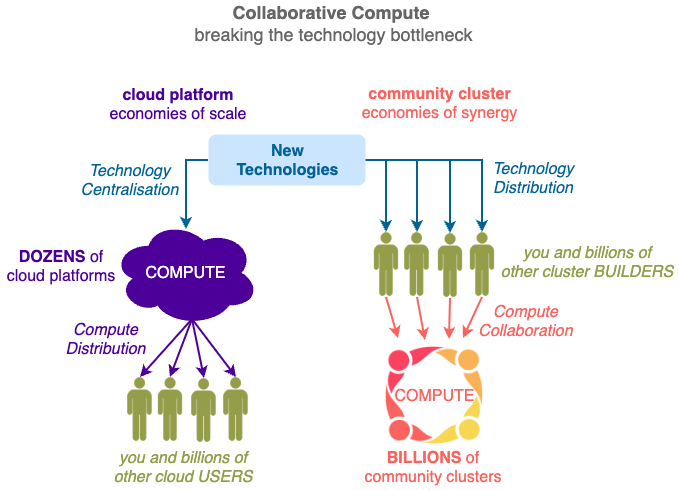
Community Cluster enables resources to be EXCHANGED efficiently and equitably in a TRUSTED manner with protected privacy, rewarded contribution and assured quality. Everyone can collaborate and be compensated for solving intractable problems (e.g. covid19, online fraud) that challenge all governments.
1.2. How does Community Cluster work ?
How does Community Cluster work ?
Separation of Control and Process
Compute is made up to data processors and control of those processors.
Compute = Control + Process
- Currently CONTROL and PROCESS of your data are centralised together (Cloud Platforms)
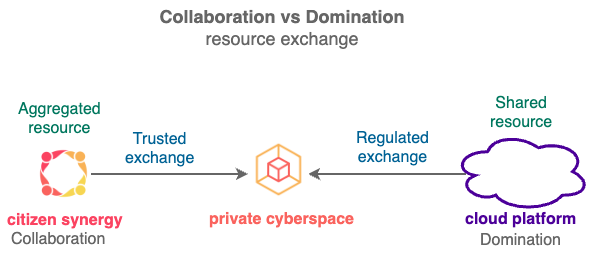
- Citizen Synergy enables otehrs to PROCESS your data without giving up CONTROL (you)
Citizen Synergy removes the COST and SKILL barriers to private cyberspace ownership by aggregating surplus resources from others and taking over data income from the Cloud. Everyone now have abundant compute power to operate RELIABLY at any scale, no matter their wealth.
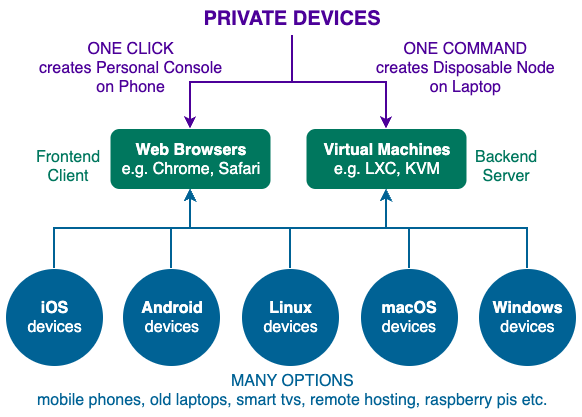
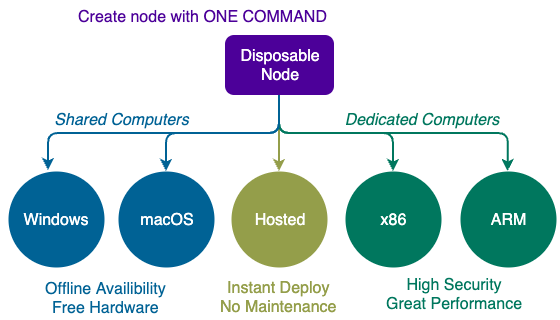
The individual Private Cyberspace owner only needs a low end mobile phone (just wifi will do - mobile phone carrier optional) to run the Personal Console software in order to control thousands of community computers with Disposable Node software worldwide.
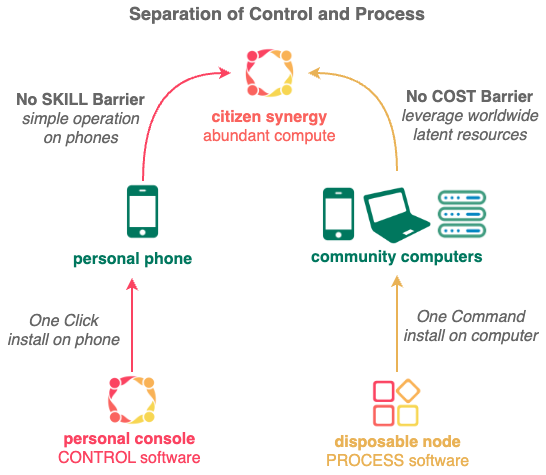
This separation of CONTROL (using Personal Console software on personal phone) from PROCESS (using Disposable Node software on community computers) is a paradigm shift from traditional monolithic computing where everything is done centrally on Cloud Platforms.
Private Cyberspace is the world's first deployment of homomorphic encryption at scale, enabling individuals to leverage the massive latent resources within the community safely, thus removing the traditional cost and skill barriers that have prevented people from acquiring reliable compute power.
Under the protection of homomorphic encryption, data can now be stored and processed securely on community computers with the easy ONE COMMAND installed Disposable Node software, to take advantage of any excess resources available worldwide (e.g. idle bandwidth overnight, unused disk space, data collected while shopping, laptops with broken screens, surplus solar energy during the day, bored retirees etc.).
2. Personal Console
With just ONE CLICK you can install the Personal Console software into your web browsers instantly.
- NO download from App Stores or Play Store
- NO sign-up to any service or create any account
- NO contacts e.g. username, email, phone number etc. needed
- NO advertisement or any unsolicited interruption
- NO leaking of data outside of your phone
- NO charge for use, distribution, modification (refer to license)
- NO hidden operation (source code is published publicly)
After installation, you can create your first piece of Information Asset in your Private Cyberspace within One Second by following the tutorial in the Quick Start Guide.
After you gained some experience the Personal Console on your phone, you can optionally extend it with more personal devices.
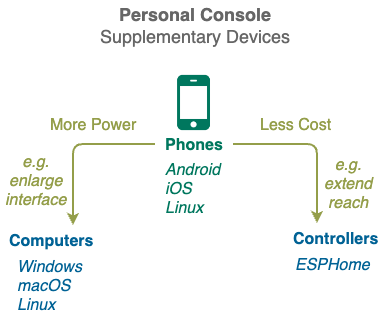
Personal Console Computers gives you more compute power as well as bigger screens and keyboards to enjoy your cyberspace in comfort. Most computers with web browsers (e.g. laptops, desktops and even TVs) can be used. The only condition to running Personal Console software on your device is that you must have exclusive control of it.
Personal Console Controller gives you unprecedented power in monitoring and controlling the physical world by letting you sprinkle low-cost low-power sensors and actuators around your environment. The more controllers you deploy, the bigger your cyberspace footprint and the more opportunities to sell its capabilities to other cyberspaces.
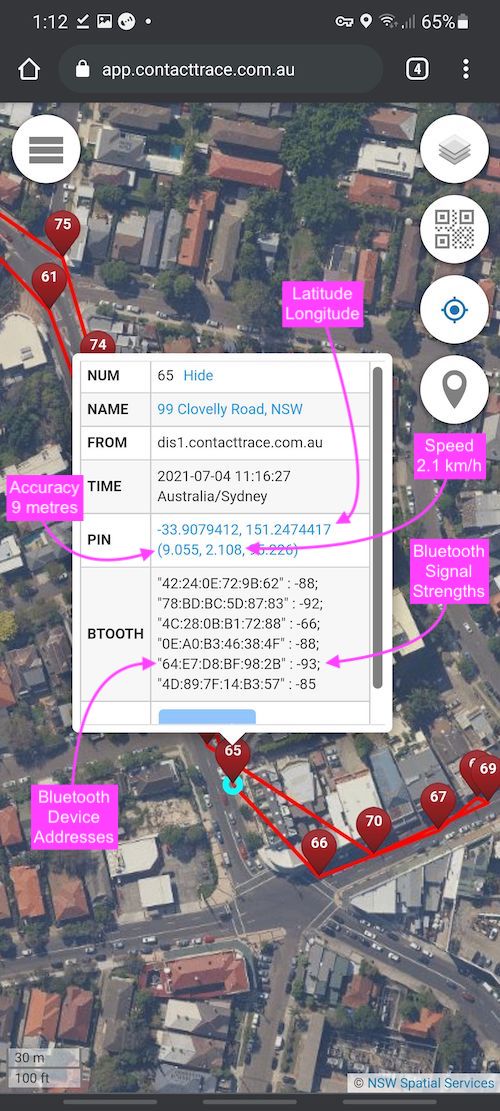
Above screen capture of a Personal Console shows a walk to the local bakery, notice some information collected about the owner (walking speeds) and the surrounding environment (bluetooth signals).
1. Unlocking Latent Resources
Citizen Synergy is a grassroots movement to boost nationwide economy by enabling trusted exchange of latent resources within the community.
One such latent resource is data locked up inside cloud platforms, which can only be manipulated using proprietary algorithms and innovated under restrictive rules. Citizen Synergy puts those data back into the economy in 3 steps:
- Empower everyone (from billionaires to refugees) to secure their data inside their private cyberspaces, with just one click on their phones.
- Leverage latent compute resources (e.g unused disks, idle computers, excess solar, bored retirees etc.) within the community to store and process data in private cyberspaces.
- Redirect income from cloud platforms by enabling private cyberspaces to deliver insights and impacts of value to others, securely and equitably, without exposing the actual data they are based on.
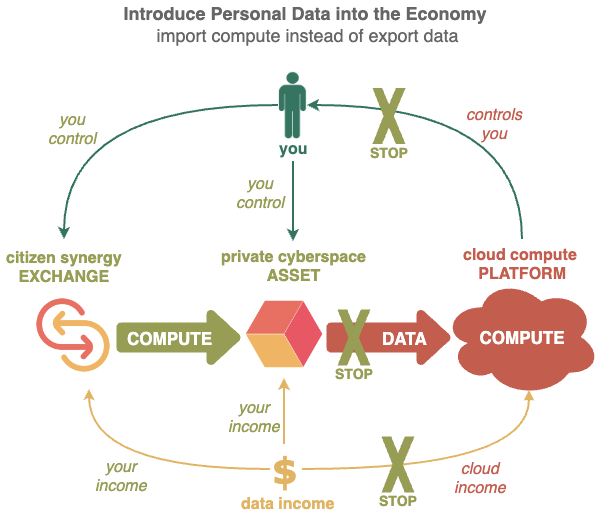
Personal data available from private cyberspaces are substantially more valuable that data locked up inside Cloud Platforms.
- Private cyberspaces can deliver superior insights since they have access to the most detailed and complete data of their owners, without any restriction from privacy laws. Most insights will be for the owner’s eyes only, from using AI to privately classify faces of family and friends to finding out the last TEN times the toilet was visited or a dress was worn ... the possibilities for increasing self-awareness, and thus improving personal productivity, are endless.
Citizen Synergy enables private cyberspaces to exchange resources in a safe and trusted manner, in order to deliver large impacts. The contact tracing exchange demonstrates how millions of mobile phones working together can supply enough data and processing power to handle large outbreaks that have overwhelmed all government contact tracing systems worldwide.
Any group (from friends to governments) can set up their own Citizen Synergy exchanges on their computers, with just one command (even on old laptops with broken screens and keyboards). The computers then work together as a team, increasing capacity, security and reliability of their exchanges. Citizen Synergy exchanges have been on limited trial in New South Wales for almost a year, with planned general availability worldwide in early 2023. Anyone can join the trial by creating a private cyberspace and with just one click.
2. Consumer Driven Productivity
Consumer data allow producers to see much wider, deeper, faster than ever before; resulting in more relevant, focused industrial outputs and enabling optimal use of all other inputs like labour, land, energy etc.
Deep real-time visibility into the whole population (previously available only to cloud platforms) can benefit every producer.
Consumers become small producers with their data output, directly contributing to improving the productivity of all industries.
3. Privacy vs Visibility
Citizen Synergy solves the privacy vs visibility conundrum by allowing insights to be extracted by producers from consumers data, but does not disclose the actual data themselves.
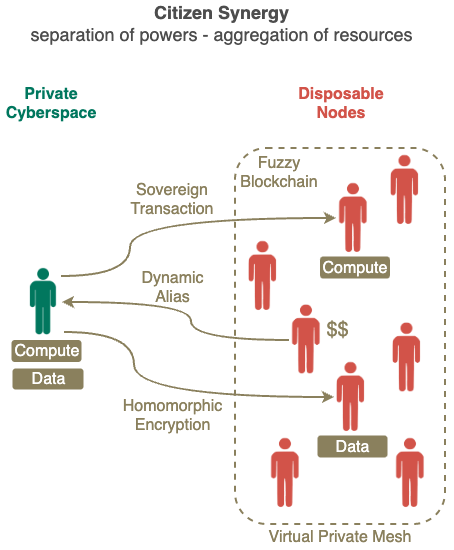
Consumers use dynamic aliases to send fuzzy data (instead of raw data) into the exchanges, which then use homomorphic encryption to process their data. Producers do not have direct access to the fuzzy data, they only get the results of their queries back from the exchange.
Every transaction is logged on non-speculative blockchains and checked by the exchange independently, so producers can be assured of the quality of the query results and consumers can be assured that all contributions made can be compensated.
Citizen Synergy is a combination of a number of breakthrough technologies.
-
Sovereign Transaction is the FIRST in the world to deliver Homomorphic Encryption at scale, enabling Public Applications dealing with massive amount of sensitive data (e.g. daily movements of whole population) to be deployed securely.
-
Fuzzy Blockchain is the FIRST in the world to deliver Truely Decentralised public blockchains without the concentration of power at the blockchain creators, miners, exchanges and whales.
also enables the Personal Applications to take advantage of the sharing of idle resources (like spare disk capacities) in a secure and efficient manner.
4. Designed to Scale
1. Citizen Synergy
The Citizen Synergy technology was developed to solve the Privacy and Visibility conundrum plaguing all COVID responses worldwide. It safely brings the latent compute power and personal data on millions of citizen mobile phone into the pandemic fight - with just ONE CLICK.
This instant boost in computing power across the whole population can be used to improve many OTHER aspects of citizens' lives, for the first time they can innovate, gain insight, earn income, make impact freely outside the restrictions of centralised Cloud Platforms.
2. Digital Equity
Citizen Synergy delivers universal personal computing to everyone, preventing those WITH massive compute power shaping the lives of those WITHOUT.
Citizen Synergy delivers 2 features not available on Cloud Platforms:
- Separation the Powers gives you many cyberspace choices and protects your data.
- Aggregation of Resources gives you access to massive compute power cheaply.
Unlike branches of a government which separate powers at the top, Citizen Synergy separates powers at the bottom - everyone is independent. It breaks up monolithic corporate owned Cloud Platforms into millions of user owned Private Cyberspaces, preventing the control of your digital life by others.
Each Private Cyberspace can seamlessly leverage the idle resources (storage, bandwidth, data, human etc.) in millions of other cyberspaces. Anyone, from billionaires to refugees, with any background can create and grow cyberspaces without limit.
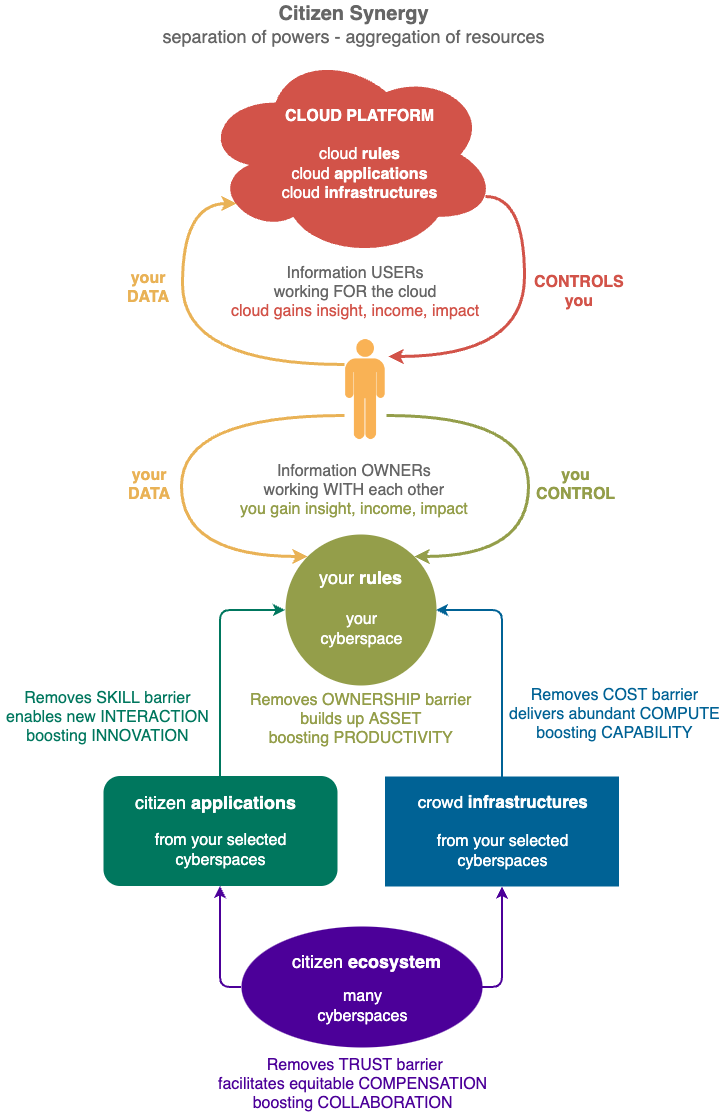
Citizen Synergy separates internal functions of Cloud Platforms into 4 independent functions run by different parties:
-
Private Cyberspace for your information assets can be created with One Click. Be an information OWNER instead of user, stop giving data and control to the Cloud. INNOVATE freely, add new dimensions to your digital life - gain insights, earn incomes and make impacts that are only possible with ownership.
-
Citizen Application revolutionises online SECURITY by resolving the Privacy vs Visibility conundrum. Unparalleled safety enables your cyberspace to interact with more people in more ways, boosting PRODUCTIVITY, solving intractable problems (covid19, online fraud etc) that challenge all governments.
-
Crowd Infrastructure makes your cyberspace COST insignificant by leveraging surplus resources from others and taking over data income from the Cloud. With an unlimited supply of affordable compute power, your cyberspace can operate RELIABLY at any scale no matter your skill and wealth.
-
Citizen Ecosystem provides a distributed trustworthy storage of RECORDS so all citizen contributions, no matter how small, can be compensated equitably. Creating an unprecedented COLLABORATIVE environment to underpin the citizen applications and crowd infrastructures used inside your cyberspace.
Private Cyberspace gives you ownership of your information by enabling you to independently and easily CONTROL how your information is to be collected, processed, stored and shared by the other 3 modules.
3. Personal Console
You can create your own Private Cyberspace by installing the Personal Console software onto your mobile phone with just ONE CLICK. From there you can take advantage of resources provides by YOUR preferred Private Cyberspaces, software resources through Citizen Applications and hardware resources through Crowd Infrastructure.
Personal Console fuses online and physical data together to give you breakthrough situation awareness and automated responsiveness.
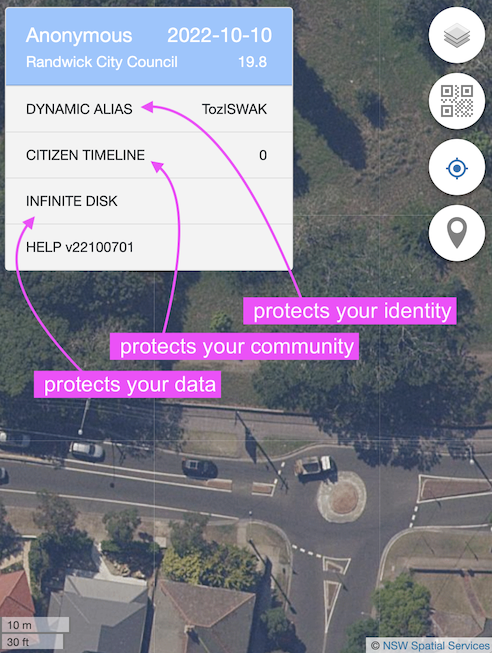
It comes preloaded with 3 Citizen Applications to boost your online and physical safety to unprecedented levels:
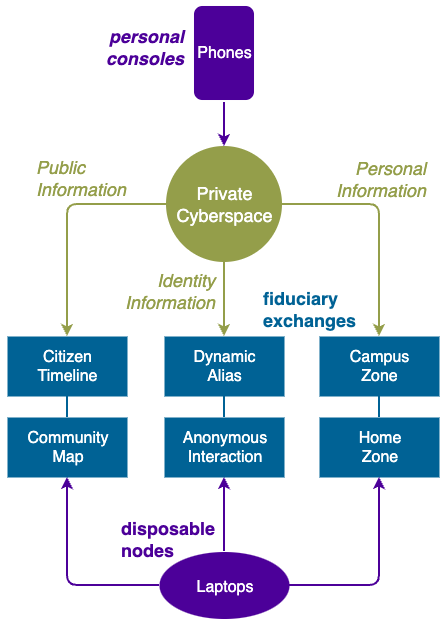
- protect you identity - Dynamic Alias
- protect you community - Citizen Timeline
- protect your data - Infinite Disk
3. Aggregation of Resources
Although Separation of Powers is good for privacy and sovereignty, the many smaller entities created as a result can have too little resources to be effective.
Citizen Synergy combines the resources within those private cyberspaces for the benefit of communities and individuals under the coordination of Citizen Ecosystems.
Citizen Synergy has been designed specifically to address that problem by aggregating numerous tiny resources together into a seamless whole, creating force multipliers in both the software (Citizen Applications) and hardware (Crowd Infrastructures) domains.
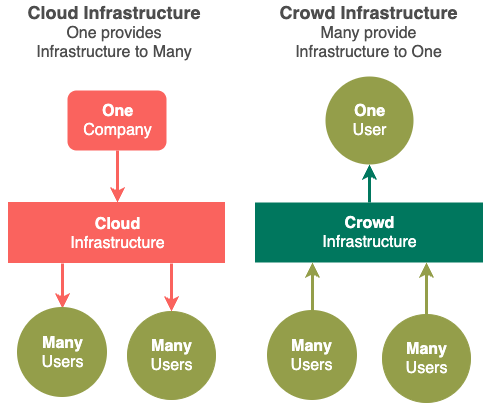
Massive improvements in price/performance is possible since Citizen Synergy turns the existing Cloud Computing one-to-many resource delivery model into a many-many resource delivery model. Enabling cyberspace owners to benefit from each other's resources seamlessly via its fine grained reward system.
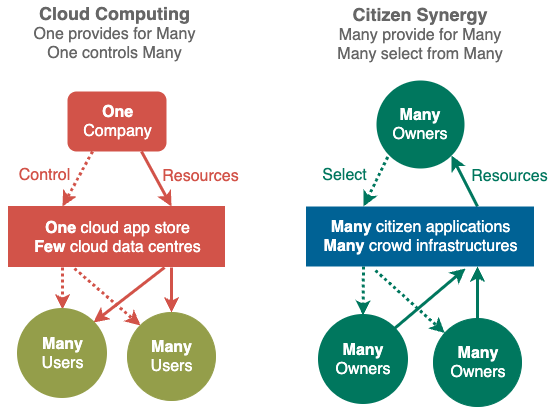
Currently, the progress of the whole world's information technology is being held back by the innovations of a few Cloud Platforms.
Citizen Synergy breaks the Cloud innovation bottleneck by enabling anyone with a good idea innovate with the Productivity breakthroughs of Citizen Applications and Reliability breakthrough of Crowd Infrastructures.
Numerous software projects are created everyday (there are more than 100 million public software repositories in Github alone), Citizen Synergy rewards contribution to software
just like other citizen contributions - equitably through Retrospective Reward.
By eliminating the skill and wealth barriers to information ownership, Citizen Synergy delivers unprecedented privacy, security, performance, and reliability to everyone.
Community Cluster
Community Cluster is a practice realisation of many collaborative concepts like collective impact.