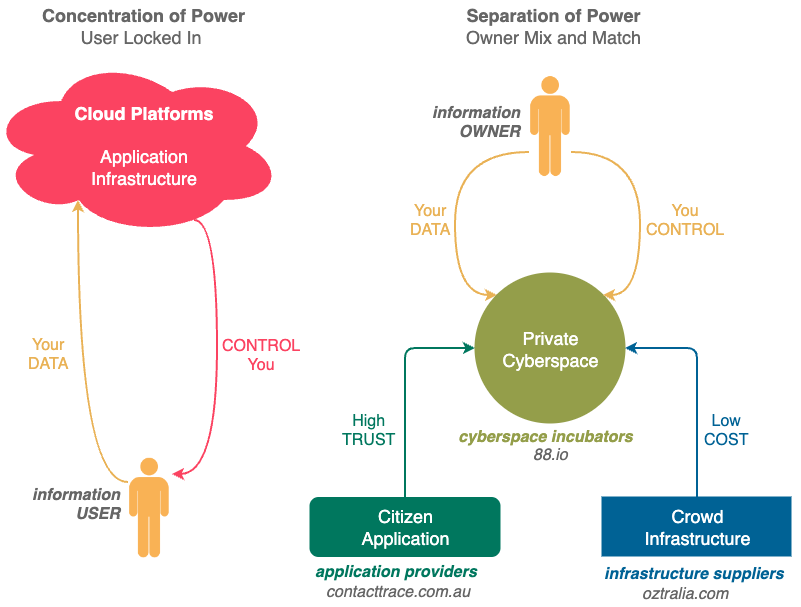
OZtralia (oztralia.com) is a Private Cyberspace Infrastructure Builder in Australia, we supply components for you to build out your own Private Cyberspace as well as provide assembly services to those who do not want to get their hands dirty.

We provide the necessary infrastructure for you to built your Private Cyberspaces at breakthrough price points and ease of use, so everyone can participate in this computing revolution, irrespective of their wealth and technical abilities.
We are also a builder incubator, happy to help others get started on their infrastructure building journeys in Australia and overseas. Currently, the languages we can provide technical support in are English (preferred), Chinese, Korean and Indonesian.
Join a Community Cluster in your local area today ... none yet ?
We can start a new cluster up in your neighbourhood!
Online Shop
Our online shop is currently in PREVIEW mode at:
https://shop.oztralia.com
you can browse around to get a feel of the products and services we will be offering in the near future.
Buy Back
Buy Back allows you to change your mind at any time until the factory warranty expires.
For example:
- Mesh Stations we sell normally have 1 year warranty - we will buy back within the first year.
- Hard Disks we sell normally have 5 year warranty - we will buy back within the first five years.
At anytime within the factory warranty period, if you decided that you do NOT want a working device that you have purchased from us anymore, you can send it back to us and we will pay you the device's original price (excluding taxes, transports etc.) adjusted by the remaining months under warranty.
If a device is in good working order AFTER warranty period, then buy back may still be offered for another 2 years AFTER the end of the warranty at the same price as if there is one month of warranty left.
If the device is faulty under warranty, you need to claim the factory warranty as normal.
If the device is faulty after warranty, you can donate it to your local Community Cluster's repair shop.