MyQ
MyQ has blocked 3rd Party Access:
Anyway, it was never a good idea even when it worked, since your data is being send to their servers in the cloud.
As mentioned in the link, to open your garage door, try to get fully LOCAL solutions like:
Apple
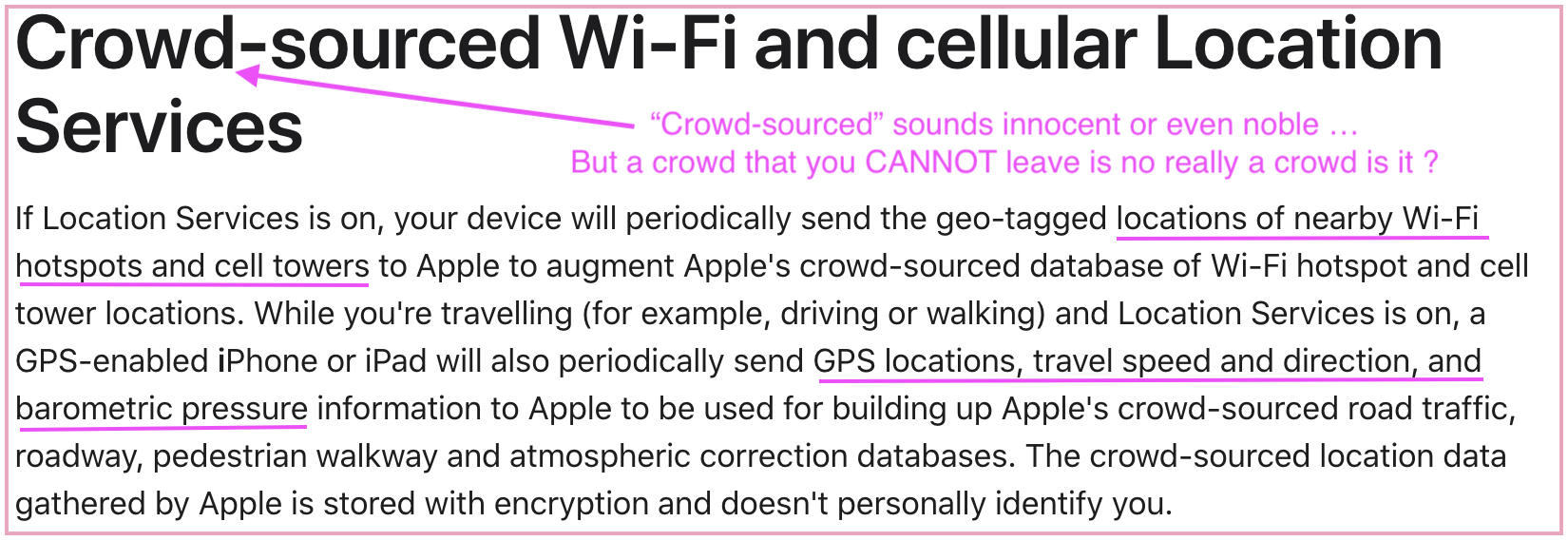
Besides give up your own privacy completely with Apple, you are also increasing Apple's ability to locate other people as well - for free. If you use Apple's location service, you have NO way of opting out performing free data collection for Apple.
source: Apple AU
You contribute to Apple data collection capability by providing free battery power, network bandwidth, physical access etc. to it, so Apple can collect data on mobile networks, wifi and bluetooth around you - without giving anything back to you - no money and not even the data you have collect for Apple.
Whatsapp Monitoring
Translated from:
2025-09-05
Surveillance and attack using delivery confirmations
An interesting, technically sophisticated attack uses delivery confirmations from messengers—without the victim noticing. This makes it possible to intercept when the phone is being used, what devices are being used, or when the victim is at home or in the office, for example.
… By using this technique at a high repetition rate, we demonstrate how an attacker can extract private information , such as tracking a user across multiple companion devices, inferring their daily routine or recent activities. Furthermore, we can infer the number of currently active user sessions (i.e., primary and companion devices) and their operating systems, as well as launch resource exhaustion attacks , such as depleting a user's battery or data allowance without any notification on the target site. …
(Emphasis added later)
This is not a case of exploiting a bug, but rather a necessary implementation that is simply being used (abused) as an alternative.
Article from heise.de from August 12, 2025: What WhatsApp and Signal reveal despite encryption... (external)
Source: Careless Whisper: Exploiting Silent Delivery Receipts to Monitor Users on Mobile Instant Messengers (external); PDF (external)
Spying on online status
Technically, it is easier to (also illegally!) monitor and spy on friends and/or strangers using their online status, as a security gap has long been unnoticed:
Messenger users could be monitored using a simple trick. Dutchman Loran Kloeze and US software developer Robert Heaton explain on their websites how easy it is to monitor other WhatsApp users. The vulnerability lies in the online status , from which specific information can be retrieved. All that is needed for surveillance is the victim's phone number.
The online status is systematically monitored by a Chrome extension while Web WhatsApp is running. Regular checks create an activity log, which in turn allows conclusions to be drawn about the user's daily routine – for example,
- when he works,
- goes to bed, or
- whether he slept through the night.
Even "hiding" the online status does not help the user in this spying case. By comparing two phone numbers , it is also possible to find out whether
- two people communicate regularly and
- what time they do this.
At first glance, the spied information seems unspectacular and is unlikely to pose a major problem for most users. Nevertheless, the security vulnerability allows for the creation of detailed user logs, for which advertisers or other interested parties would pay a lot of money. In the worst case, the collected data could be misused for criminal purposes.
WhatsApp statement:
In short: WhatsApp is aware of the vulnerability but does not see it as a security problem.
Demonstration / Experiment
Here are the (English) explanations of how it works. Both experiments require that "WhatsApp Web" is running in your browser.
1. Chrome extension by Loran Kloeze
This Chrome extension displays many consecutive phone numbers in a freely selectable range .
Source: https://github.com/LoranKloeze/WhatsAllApp (external)
2. Robert Heaton and his “4-line code”
// NOTE - Requires jQuery
setInterval(function() {
var lastSeen = $('.pane-header .chat-body .emojitext').last().text();
console.log(Math.floor(Date.now() / 1000) + ", " + lastSeen);
}, 1000);
… which only needs to be changed from “lastSeen” to retrieving the “online status”.
Source:
https://robertheaton.com/2017/10/09/tracking-friends-and-strangers-using-whatsapp/ (external)
3. OnlineStatusMonitor
The University of Erlangen-Nuremberg also demonstrates the possibilities of monitoring with its "Online Status Monitor" project (external) . Unfortunately, this site is also only available in English.
Ethical Considerations (translated from the website content)
To protect the privacy of each randomly selected user, all statistics described in this section are based on anonymized data. Although we tracked each user's exact online time over several months, we decided not to publish this data, providing only average cumulative statistics. In addition, we took some additional measures, such as blurring profile pictures and masking individual phone numbers. The dataset will be used for research purposes only and will not be shared. These measures allow us to demonstrate the practical relevance and impact of constant surveillance of messenger users while ensuring that the privacy of each randomly selected messenger user is maintained.
4. Scientific paper(s)
University of Ulm (2014)
Scientific study (2020)
In a collaborative study between TU Darmstadt, TU Graz and the University of Würzburg, it is shown that currently used methods for mobile contact tracing pose a massive threat to users' privacy:
Quote: Our study of three popular mobile messengers (WhatsApp, Signal, and Telegram) shows that, contrary to all expectations, so-called crawling attacks are possible on a large scale. Using an accurate database of mobile number prefixes and very limited resources, we were able to query 10% of all US mobile phone numbers for WhatsApp and 100% for Signal. Regarding Telegram, it turns out that its API exposes a range of sensitive information, even about phone numbers not registered with the service.
Source: https://contact-discovery.github.io/de/ (external)
Excursion MS Teams
Spying on status isn't unique to WhatsApp. For example, Microsoft Teams has a feature that notifies you of a status change for up to 16 contacts. This can't be disabled in the settings, so every user (colleagues, employees, and managers) can automatically check the status of these contacts.
This feature in MS Teams seems even more worrying and real because the exploitation is very low-threshold and can be carried out immediately by any user.
Notes
Nothing to hide? Systematic recording of status can also lead to bullying or even defamation of individuals. But even under labor law, recording and evaluating status for the purpose of monitoring performance and behavior is certainly not permissible—especially with regard to data protection.
Important:
The information and the script are for demonstration purposes only and may only be used for monitoring if the persons concerned consent !
Notes:
- The script is not intended to spy on or denounce people, but rather to demonstrate the ease of implementation and the potential danger.
- Use at your own risk.
- Requests to change/adapt the script will not be answered.
Everything technically possible is being done – WhatsApp spying is no exception. But even the "misbehavior" of centralized services (Google/WhatsApp/Facebook, etc.) should not serve as a justification for one's own "spying."
Important:
Spying on the privacy of friends/acquaintances/strangers is immoral, rude and may even be illegal/punishable!
Sources:
https://www.hna.de/netzwelt/grosse-sicherheitsluecke-bei-whatsapp-entdeckt-zr-8318025.html http://www.chip.de/news/WhatsApp-Sicherheitsluecke-erlaubt-Ueberwachung-von-Freunden_124936240.html
English:
https://www.lorankloeze.nl/2017/05/07/collecting-huge-amounts-of-data-with-whatsapp/
https://robertheaton.com/2017/10/09/tracking-friends-and-strangers-using-whatsapp/
https://www.onlinestatusmonitor.com
Further information
In addition to this topic, the following information is provided here:
Whatsapp Cannot Delete
Translated from:
Whatsapp collects your data even if you don't use the messenger
04 Jul 2021
- Link copied!
You don't use WhatsApp because you want to protect your personal data? That's less helpful than you think.
Shutterstock
Ever since Whatsapp became part of Facebook, some users have stopped using the messenger for data protection reasons.
However, even if you have deleted your account and uninstalled WhatsApp, Facebook can still access much of your data.
The reason for this is your contacts who continue to use the service and have saved your data in their digital phone book.
Just a few days ago, WhatsApp announced in a blog post that it had surpassed the two billion user mark – Business Insider reported . This further extends the short messaging service's lead over its competitors.
Nevertheless, many users decide not to use the Facebook -owned service because they want to protect their personal data.
Read also: Why you shouldn't use the WhatsApp camera
But even if you delete your Facebook account and ban WhatsApp from your smartphone, the messenger can still access much of your data.
Whatsapp: Data collection continues even without an account
To gain access to your data, WhatsApp does not need any hidden backdoors, but simply accesses the digital phone books of your contacts.
For example, if your best friend has saved your birthday, your place of residence, your email address, your phone number(s), the names and dates of your family, your website, your Twitter name and various other data under your name and grants WhatsApp access to the phone book, the messenger will also read all of this data.
So if you really want to make sure that WhatsApp and Facebook know as little as possible about you, you have to tell all your contacts to delete any data that goes beyond the bare essentials from their phones.
Signal
Translated from:
Generally
Signal has no real advantages over WhatsApp:
Both systems are centralized and de facto closed systems; the company is headquartered in the United States of America (USA). Both use virtually the same encryption technology (Signal, slightly modified since 2023 as PostQuantum Encryption ), and registration is exclusively based on the phone number. Both also use IT infrastructure in the USA; the server software is not consistently transparent (not always open source), the server software can be modified without the user's knowledge (which has already happened with Signal), and neither uses international standards, which prevents easy and true interoperability . With both WhatsApp and Signal, you are dependent on a central location .
Co-founder Matthew Rosenfeld (aka "Moxie Marlinspike") stepped down from his position as CEO in January 2022 (external) and (as of March 2023) remains only on the board. The current CEO of Signal is his former WhatsApp co-founder, Brian Acton.
-
Positive: good end-to-end encryption with “ Axolotl ” (external; PDF file), which is the basis for many other implementations
-
Positive: good lobbying; “official recommendation” from Edward Snowden
-
positive: Client is completely open source
-
Positive: own servers are possible (but these are then self-contained systems)
-
Negative: "...when using Signal, data protection concerns remain , primarily because this service processes its users' personal data outside the scope of the GDPR. The use of this messenger service cannot therefore be recommended." Source: EKD (external; PDF file dated October 24, 2018)
-
Negative: File size limits for video, audio, and documents max. 100 MB (external), for GIF files max. 25 MB (external)
-
negative: central service - no interoperability
-
Negative: the server software actually used may not match the version published on GitHub
-
Negative: Terms of Use (external) and Privacy Policy only in English
-
negative: only phone number as identifier (regardless of whether with/without hash)
-
negative: no federation with other servers
-
Negative: No registration/use possible without a smartphone
-
Negative: no multi-device capability (using one chat account on multiple independent devices)
-
negative: the desktop application is based on Electron
-
Negative: Forks of the Signal app are not allowed to use the Signal server
-
Negative: Weaknesses in authentication for encryption
-
Negative: Minimum age 13 years (may vary by country)
-
negative: cryptocurrency “Sentz” (formerly “MobileCoin”)
-
Negative: does not use its own servers but Amazon infrastructure
At this point, I'd like to point out again: If you find any incorrect or outdated information, please let us know! >> Contact <<
Criticism according to Wikipedia (external):
"The foundation behind Signal has been criticized for its lack of transparency, its lack of a published charter, and its failure to publish detailed financial or annual reports. Furthermore, its decision-making structures are hierarchical and power is highly concentrated. Signal has not designated a data protection representative to the authorities, as required by EU law. Attempts by the authorities to contact the company remain unanswered."
Telephone numbers
Hash values from phone numbers are not a security feature, because phone numbers can easily be reconstructed from the hash values (keyword: "rainbow table" (external)). Signal also sends each individual user a registration SMS. The number may not be transmitted to Signal in plain text, that may be true – but at the very latest, it is known during registration, and thus they know every user's number. This includes internal phone numbers or PIN numbers of companies, government agencies and organizations with security responsibilities (BOS), or women's shelters that use Signal. That's all fine – of course not!
Signal ensures that the hashes of phone numbers are stored on a dedicated server. Why? This means that they don't offer any additional security but are just as worthy of protection as the corresponding phone numbers. Besides, it doesn't matter where the hashes (=phone numbers) are stored on Signal – they are stored.
Signal also accesses the user's entire phone book, allowing you to see who in your circle of friends is using Signal. This means you can't select individual users with whom you want to communicate via Signal, and you can't keep your own access private.
Cryptocurrency
The name has been changed from "MobileCoin" to "Sentz" (external) (the original internet address "mobilecoin.com" is automatically redirected to the new address "sentz.com").
Critical voices and reactions to Signal Payments:
- June 7, 2024: Article that also addresses cryptocurrency (English): https://bencrypted.gitlab.io/post/8 (external)
- April 9, 2021: Opinion in the Kuketz blog: https://www.kuketz-blog.de/kritische-stimmen-und-reaktionen-zu-signal-payments (external)
- 07.04.2021: Comment by Fefe: https://blog.fefe.de/?ts=9e9221ad (external)
financing
Here is some interesting information about the cost structure:
We estimate that Signal will need about $50 million a year to operate by 2025—and that's very little compared to other popular messaging apps that don't respect your privacy.
Translated from Source: https://signal.org/blog/signal-is-expensive (external)
At the end of 2023, Signal's cost breakdown for operating a large messaging platform was as follows:
- Storage: $1.3 million per year (9.3%). Interestingly, Signal doesn't store message history on the server. Message history is stored on the client.
- Servers: $2.9 million per year (20.7%). Costs for cloud servers supporting the messaging service.
- Registration fees: $6 million per year (42.9%). These are the costs for validating phone numbers and performing other validations.
- Total bandwidth: $2.8 million per year (20.0%).
- Additional services: $700,000 per year (5.0%). Uptime monitoring, outage alerts, redundant capacity for disaster recovery, maintenance contracts, etc.
- Infrastructure costs (from November 2023): Approximately $14 million per year to support 40 to 50 million monthly active users.
...and that's just the infrastructure costs. You have to add all the associated costs of running an organization with more than 50 employees.
- If a company/organization wants to operate a messaging platform on a large scale, the operating costs should be properly estimated.
- This also demonstrates the impact of a centralized approach compared to a federated model. In a centralized model, the organization operating the platform must bear all the costs of operating the platform. With a federated model like XMPP, the costs can be shared across the entire network.
Source: process-one.net (external)
Client
Replicas of the app
You can easily get Signal from the Aurora Store or download it directly as an APK from the Signal website (external), which then runs perfectly on non-Google devices.
Alternatively, you can also use Signal forks such as Langis, Molly (external), and Signal FOSS (external) via an additional F-Droid repo. According to Mr. Rosenfeld (Moxie), the use of Signal servers is prohibited for clones/forks, but perhaps Signal hasn't yet established a system to actively detect and block them. With every fork, the question arises as to whether and how the cryptocurrency code was removed, and whether Signal will then still allow the client access to the quasi-proprietary servers.
Signal itself does not want the original app to be made available via F-Droid.
Source: Github (external)
Client testing
It appears that Signal has the ability to detect "outdated" clients (or clones of the app) and then reject communication with them if necessary. An error code in the command-line tool "signal-cli" indicates this:
Error while checking account +XXXXXXXXXXX: StatusCode: 499 org.whispersystems.signalservice.api.push.exceptions.DeprecatedVersionException: StatusCode: 499
Sending and receiving messages with signal-cli also seems to throw a "DeprecatedVersionException" (as of 2022-10-05, 21:59 UTC). This exception appears to be intended to disable outdated clients.
Source: https://github.com/AsamK/signal-cli/issues/1022 (external; December 20, 2022)
server
Server code
Signal has always been praised as the security-conscious alternative to WhatsApp and other apps because of its open source nature. However, the company was "caught" using server code that did not match the public code for almost a year. Here are the published versions of the server code up to (as of) July 14, 2021, which show that many versions have repeatedly been (externally) not released in the past:
- v6.13.0 … 8 days ago
- v6.12.0 … 8 days ago
- v6.11 … 11 days ago
- v6.9 … 13 days ago
- v6.8 … on 11 Jun
- v5.98 … on 2 Jun
- v5.97 … on 28 May
- v5.96 … on 27 May
- v5.31 on 17 Feb
- v5.30 on 17 Feb
- v5.23 on 3 Feb
- v4.97 on 14 Jan
- v4.93 … on 11 Jan
- v0.93 … on 10 Mar 2016
- v0.54 … on 25 Jun 2015
- v0.53 … on 25 Jun 2015
- v0.52 … on 24 Jun 2015
- v0.50 … on 7 Jun 2015
- v0.49 … on 13 May 2015
- v0.48 … on 22 Apr 2015
The reason will be the integration of the cryptocurrency (MobileCoin), which is already completely (pre)mined.
But:
- That's okay, because the server code belongs to Signal ( https://github.com/signalapp/storage-service ) and there is no obligation to publish it!
- This clearly shows (again) the dependency that comes with using a central provider.
Notes on the license ("AGPL"):
This license applies only to anyone else who ever uses Signal code released under this license. The original authors of the code can change the license at any time. Licenses generally only apply to everyone else who does not hold the copyright or relevant usage rights to the code itself. See also Contributor License Agreement (CLA) (external). Even unreleased software (in this case, parts of the server software that have been updated) is their property. This is probably why there are no permitted merge requests from others on GitHub.
Report:
https://androidpolice.com/2021/04/06/it-looks-like-signal-isnt-as-open-source-as-you-thought-it-was-anymore/ (external; English)
Problem: The process highlights the dependency and it cannot be ruled out that something like this could happen again.
Server use prohibited
Mr. Rosenfeld (“Moxie”) has labeled OpenSignal a “product” and prohibited them from accessing the official Signal servers or having anything with Signal in their name:
I'm not OK with LibreSignal using our servers, and I'm not OK with LibreSignal using the name “Signal.” You're free to use our source code for whatever you would like under the terms of the license, but you're not entitled to use our name or the service that we run.
If you think running servers is difficult and expensive (you're right), ask yourself why you feel entitled for us to run them for your product.
On the question about server federation :
It is unlikely that we will ever federate with any servers outside of our control again, it makes changes really difficult.
Source: https://github.com/LibreSignal/LibreSignal/issues/37#issuecomment-217211165 (external; English; May 5, 2016)
Encryption
Encryption also requires authentication, because without authentication, even the best encryption is useless. But Signal (apparently) has a weakness:
_“… Unfortunately, Signal's default authentication scheme is weak. It is arguably worse than
Source: sequioa-pgp.org (external; English)
I understand that PGP and authentication are great and important ideas, but unfortunately they no longer have a place in the modern world. Moxie Marlinspike
Source: wanted
Man-in-the-middle attack
Signal is technically capable of compromising E2E encryption through a simple man-in-the-middle attack because the entire key exchange is mediated by the provider. While Signal offers security code verification, it is optional and still requires a trusted out-of-band channel that doesn't replace messages (one of the criticisms of SimpleX), and it isn't prominently displayed in the Signal app when the security code changes. Experts' view that a small portion of users using this feature protects all users is misleading, as it only protects against large-scale attacks where all (or a significant portion) of users would be compromised, but it offers poor defense against targeted attacks—users must be diligent about re-verifying the security code whenever a change occurs, and in some cases, finding a reliable out-of-band channel can be very difficult. Therefore, I would argue that Signal cannot be used as a platform for mission-critical secure communications, as Signal servers can trigger key renegotiation at any time, and this would require an out-of-band security code review to confirm that the cause was caused by contacts changing devices and not a compromise - affected users cannot confirm this in the Signal conversation, as users no longer have proof of who they are communicating with once the security code is changed.
Source: reddit.com (external)
Encrypted database
Next time someone asks about “encrypted database (because Signal does that too)” …
iOS: https://blog.elcomsoft.com/2019/08/how-to-extract-and-decrypt-signal-conversation-history-from-the-iphone/ Android: https://www.cellebrite.com/en/blog/cellebrites-new-solution-for-decrypting-the-signal-app/
There is a small cross-platform tool (script) for exporting the Signal Desktop database (“Cross-platform decryption and export utility for Signal Desktop”): https://github.com/aaronsdevera/sigkill (external). A description can be found on Github (external; PDF).
Secure data recovery
The “secure value recovery (SVR)” is also under criticism: blog.cryptographyengineering.com
Post-Quantum Encryption
Since September 2023, Signal has implemented a slight modification of the original encryption technique (technically known as Extended Triple Diffie-Hellman Handshake (X3DH)) as "Post Quantum." From their documentation:
This document describes the "PQXDH" (or "Post-Quantum Extended Diffie-Hellman") key agreement protocol. PQXDH establishes a shared secret key between two parties who authenticate each other based on public keys. PQXDH provides post-quantum forward secrecy and a form of cryptographic deniability, but even in this revision of the protocol, it relies on the hardness of the discrete log problem for mutual authentication. …
Source: signal.org (external; machine translated)
Currently, it is only a minor modification of X3DH [the original Signal protocol]... This design enables protection against passive quantum adversaries and prevents "harvest now, decrypt later" approaches. However, the protocol does not add PQ-secure mutual authentication and would thus be vulnerable to an active quantum attacker. This is a very deliberate decision, as this simple design ensures a high degree of deniability.
Source: HU Berlin (external; machine translated; commentary and formatting added)
Surveillance and attack using delivery confirmations
An interesting, technically sophisticated attack uses delivery confirmations from messengers—without the victim noticing. This makes it possible to intercept when the phone is being used, what devices are being used, or when the victim is at home or in the office, for example.
… By using this technique at a high repetition rate, we demonstrate how an attacker can extract private information , such as tracking a user across multiple companion devices, inferring their daily routine or recent activities. Furthermore, we can infer the number of currently active user sessions (i.e., primary and companion devices) and their operating systems, as well as launch resource exhaustion attacks , such as depleting a user's battery or data allowance without any notification on the target site. …
(Emphasis added later)
This is not a case of exploiting a bug, but rather a necessary implementation that is simply being used (abused) as an alternative.
Article from heise.de from August 12, 2025: What WhatsApp and Signal reveal despite encryption... (external)
Source: Careless Whisper: Exploiting Silent Delivery Receipts to Monitor Users on Mobile Instant Messengers (external); PDF (external)
GDPR
There are no German terms of use and no German privacy policy. Are the English versions legally valid in Germany? Regardless, Signal states in its introductory remarks on the GDPR (external):
Signal messages and calls cannot be viewed by us or third parties because they are always end-to-end encrypted, private, and secure.
“We are sure” is not a typo on my part - it is not the content that is interesting, but the resulting metadata (security =/= data protection).
And in the “Terms of Service” (=Terms of Use) furthermore:
Additional technical information is stored on our servers, including randomly generated authentication tokens, keys, push tokens, and other material that is necessary to establish calls and transmit messages.
… which keys are actually stored there?
The "Privacy Policy" explicitly (but unnecessarily) points out that the telephone number, profile name, and profile picture are, of course, always end-to-end encrypted - but what was that again about the metadata in central systems?!
Apparently, Google automatically detects that you are using Signal:
PING contentproxy.signal.org (107.178.250.75) = Google
Sieht man auch gut so:
$ host contentproxy.signal.org
contentproxy.signal.org has address 107.178.250.75
$ host 107.178.250.75
75.250.178.107.in-addr.arpa domain name pointer 75.250.178.107.bc.googleusercontent.com.
Why Signal runs on Amazon servers (AWS)—but this part is on Google—isn't immediately clear. Perhaps they don't want AWS to be able to intercept and correlate all access data, or perhaps they don't want the "traffic data" and "metadata" to be kept separate from each other and not on the same service provider?
At https://signal.org/blog/looking-back-on-the-front/ (external) it is at least explained why Signal does not use its own servers.
The security model with regard to metadata can be briefly described as “ trust the central operator ” because “The ecosystem is moving”…
The ecosystem is moving
Building on a presentation from 2016, Moxie (co-founder and managing director) will give a presentation on December 28, 2019, at the Chaos Computer Club ("CCC") on the topic of "The Ecosystem is Moving." This presentation will address the advantages and disadvantages of centralized and decentralized systems. Naturally, Signal is touted as the solution.
However, the Signal CEO's argument for his product is controversial and often overstated. While many of the arguments presented there are valid, the "value of freedom" is ignored. Ultimately, (for many) it's not just about technical security, but rather about future security .
Here are various sources/information on “The ecosystem is moving” (unfortunately all in English):
- May 10, 2016: Article Matthew Rosenfeld (aka Moxie Marlinspike) (external)
- 30.11.2016: Objections Daniel Gultsch (external)
- December 28, 2019: Lecture by Matthew Rosenfeld (aka Moxie Marlinspike) (external).
The lecture can also be found on YouTube (external). - 12/29/2019: Reason Matthew Rosenfeld (aka Moxie Marlinspike) for taking the video offline:
I had asked for it not to be recorded (which is what I've been doing with talks for the past 5yrs or so). Seems like there was some confusion, and it was recorded/published, then removed. …I just prefer to present something as part of a conversation that's happening in a place, rather than a webinar that I'm broadcasting forever to the world. I have less faith in the internet as a place where a conversation can happen, and the timelessness of it decontextualizes.
Source: https://nitter.net/moxie/status/1211443530335281153 (external)
- December 29, 2019: Opinion from XMPP (external)
- January 2, 2020: Opinion from Matrix (external)
Partial translation of Matrix's opinion on Moxi Marlinspike's opinion "The ecosystem is moving":
... However, all of this [the aforementioned facts] completely ignores one critical thing - the value of freedom. The freedom to choose which server to use. The freedom to run your own server (perhaps invisible within your application, in a P2P world). The freedom to choose which country your server runs in. The freedom to choose how much metadata and history to retain. The freedom to choose which apps you want to use - and still have the freedom to talk to anyone you like (without them necessarily installing another app). The freedom to connect your own functionality - bots, bridges, integrations, etc. The freedom to choose which identifiers (if any) you want to use to register your account. The freedom to extend the protocol. The freedom to write your own client or build entirely new, previously unimagined systems on top of it.
It's true that if you're building a privacy-optimized messaging app at all costs, Moxie's approach is one way to go about it. However, this results in a perversely closed world—a closed network where unofficial clients are forbidden, with no platform to build on, no open standards, and you end up putting all your eggs in one basket, trusting that past, present, and future Signal will maintain its values, stay alert, and somehow evade compromise and censorship... even though it's probably the single most valuable target on the 'net.'
Quite simply, that's not a world I want to live in.
We owe the entire success of the internet (let alone the web) to openness, interoperability, and decentralization. To declare that openness, interoperability, and decentralization are "too hard" and not worth the effort of building a messaging solution is to throw away the entire potential for vibrancy, creativity, and innovation that comes from an open network. Sure, you might end up with a super-private messaging application—but one that starts to smell alarmingly like a walled garden, like Facebook's Internet.org initiative, or an AOL keyword, or Google's AMP.
So we're happy to continue taking on Moxie's challenge to prove him wrong—to show that it's both possible and imperative to create an open, decentralized messaging platform that (if you use reputable apps and servers) can be as secure and metadata-light as Signal... and in fact, even more so, since you can run your server on the network and not have to register with a phone number, and in the future, you might not even need a server at all.
7 reasons
Here are the headlines from a detailed commentary “ 7 good reasons why you should never trust Signal ”
- The mobile phone number requirement
- Funding
2a.) Brian Acton
2b.) Open Tech Fund = Money from the US government https://www.opentech.fund/results/supported-projects/open-whisper-systems (external) 2c.) What happens when the money runs out? What happens next with Signal? - Amazon's Cloud AWS (see: https://de.wikipedia.org/wiki/CLOUD_Act )
- Noticeable “security vulnerabilities” in three US messengers – patched (closed) in the meantime, of course:
- WhatsApp from Facebook: "The attacker can easily inject the spyware into the device through a WhatsApp call, even if the called party doesn't answer." / https://heise.de/-4421379 (external)
- Apple's iMessage: "A Google security researcher describes how malicious code can be remotely injected into iPhones without user interaction." / https://heise.de/-4632972 (external)
- and the SignalApp: “Big eavesdropping call: Signal automatically accepts calls” / https://heise.de/-4546500 (external)
- Signal wants to be an SMS replacement
- Legal sphere of influence of the USA and now also the EU
- “Moxie Marlinspike” (external) is just a stage name
Source: Comment in the Heise Forum (external)
Tips
- Step-by-step guide (external; English) on how to use Signal without a smartphone
- Signal Android app directly and without Aurora/PlayStore: Download the hidden APK (external) from the Signal page - updates even without Aurora/PlayStore
Registration without a mobile number
Tip: When registering with Signal, you don't need to provide your actual mobile number. You can use a separate SIM card with a different mobile number, or even an unused landline number (this also works with a public phone number!). In this case, you'll receive the confirmation SMS with the verification code read to you over the phone.
Sources: netzwelt.de (external) / vice.com (external; English)
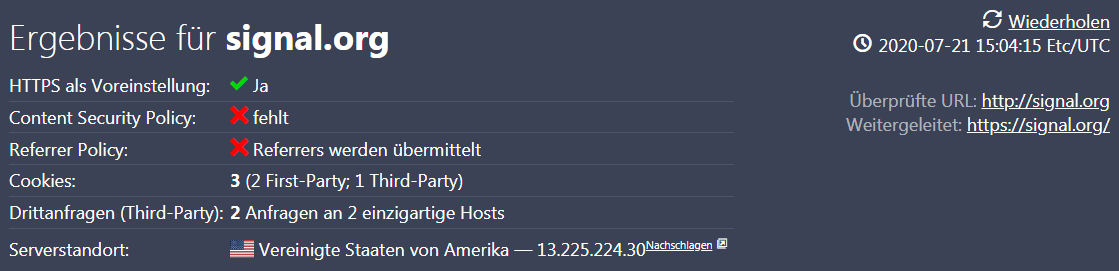
Webbkoll
Source: https://webbkoll.dataskydd.net/de/results?url=http%3A%2F%2Fsignal.org (external)References
- Project page: https://signal.org/de (external)
- Matthew Rosenfeld (aka Moxie Marlinspike): https://en.m.wikipedia.org/wiki/Moxie_Marlinspike
- German Wikipedia entry (external)
- Why not chat with Signal (all articles in English):
- August 8, 2024: https://www.moparisthebest.com/against-silos-signal (external)
- June 7, 2024: https://bencrypted.gitlab.io/post/8 (external)
- January 2, 2023: Another very good overview/article: https://restoreprivacy.com/secure-encrypted-messaging-apps/signal (external)
- 10.05.2019: Signal has numerous privacy issues that make it unsuitable for privacytools.io (external)
- 08/08/2018: I don't trust Signal (external)