Regain your Privacy and Trust - evolve from Compute User to Compute Owner with just ONE CLICK.
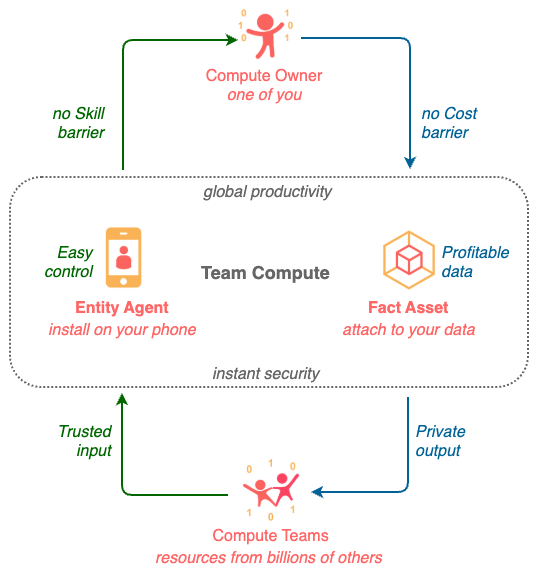
Compute Owner takes advantage of Team Compute to leverage resources from billions of others.
1. Your Own Asset
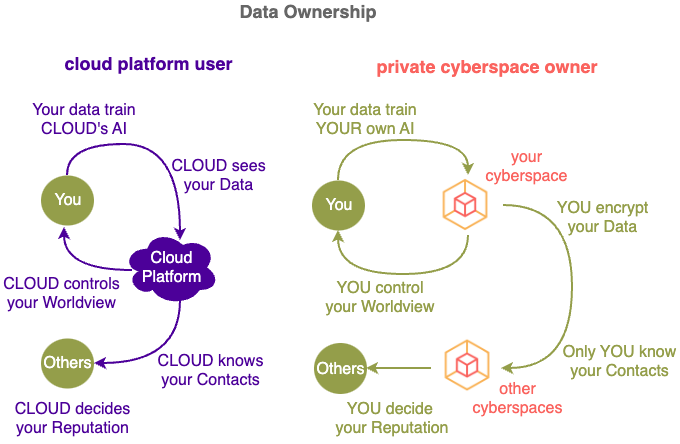
Data is your most important asset – knowing or disclosing just ONE extra piece of data could change your life.
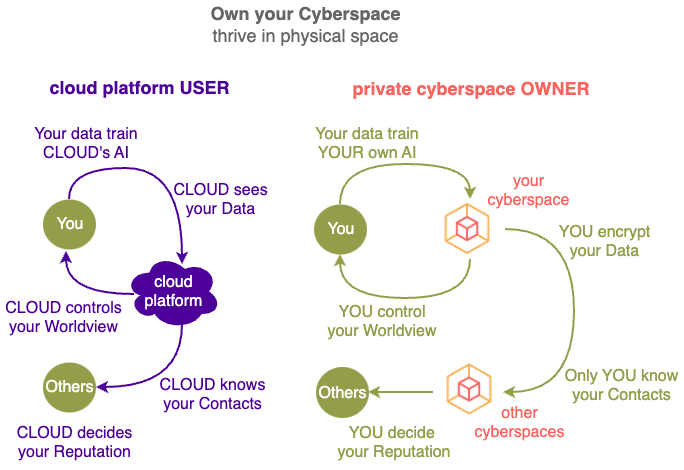
Yet currently most of your data is stored remotely in the Cloud, controlled and processed by people you have never met, all of them having DIFFERENT interests and aspirations to you.
You interact through their interfaces and you play by their rules, basically you have lost control – your most important asset is NO longer yours.
2. Removing Cost and Skill Barriers
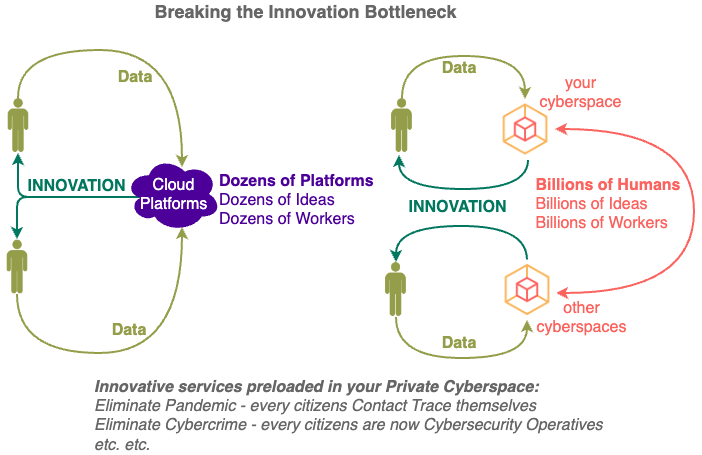
With Compute Ownership, individuals can import compute to process their data themselves instead of exporting their data to Cloud Compute, taking back the control of their digital lives and value of their data.
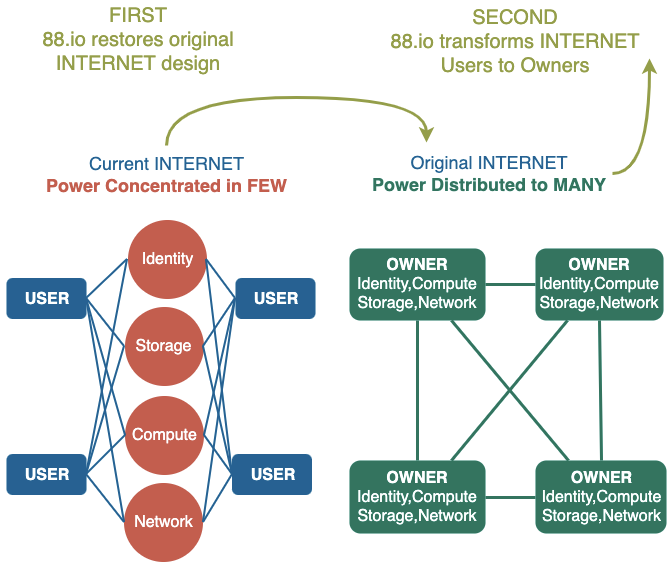
Currently Cloud Compute controls digital activities and monopolises data values worldwide, creating a global Cloud Bottleneck that stifles every aspect of modern life (from innovation to production).
Compute Ownership gives you unprecedented capabilities in your digital life by solving security and profitability problems associated with mass compute ownership.
Compute Ownership gives you unprecedented capabilities in your digital life, so well articulated in William Blake's poem, which are only available now ... more than 200 years after it was written.
Whereas previously there was simply no efficient way to tell an AI model which parts of an input image to keep, Compute Ownership changes this by introducing a method to enable Stable Diffusion models to use additional input conditions that tell the model exactly what to do
For the first time in history, both COST and SKILL barriers to compute ownership are removed.
Private Cyberspace Applications
Private Cyberspace is about giving non-technical owners EASY CONTROL of their applications.
Not everyone knows how to cook, but we all know what tastes good. If food taste bad, change the cook instead of going into the kitchen.
The same applies to the private cyberspace application.
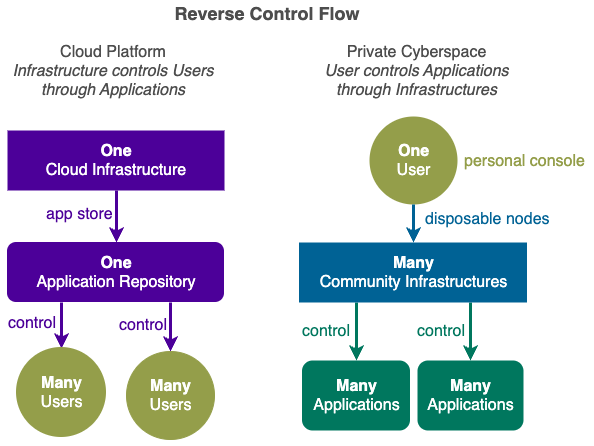
All applications inside your Private Cyberspace are under your full control of you only (no one else).
Owners interact with each other through their own private cyberspaces under their own rules without an cloud limitation.
personal application space under the exclusive control of the owner.
There are millions of free and open source applications (many resell by the cloud to you),
all your needs, wants and dreams
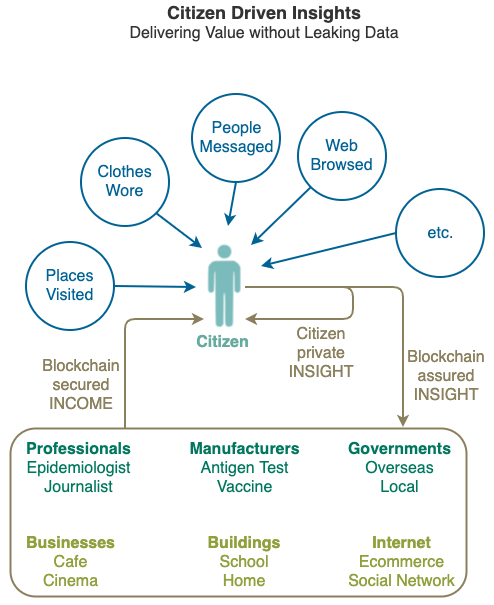
Compute Equity gives you ownership of a personal piece of the online world (through private cyberspace applications), so you can see more, earn more and do more in the physical world under your own terms by working directly with other private cyberspaces (through citizen synergy infrastructure) without depending on cloud platforms..
2.2. Citizen Synergy Infrastructures
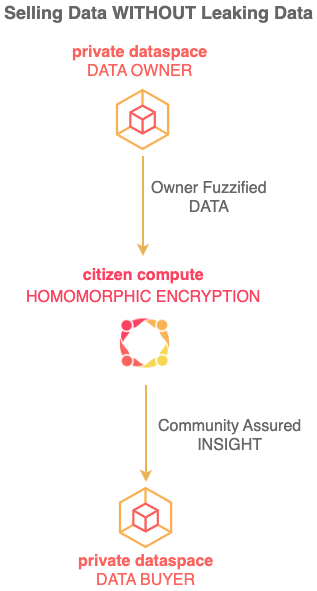
instead of sending your data into the Cloud, you process data yourself in your Private Cyberspace.
by transferring the control of your data and resulting benefits from Cloud Platforms back to you.
empower individuals to effect real world effects by giving them full control and all benefits from their data:
- establish Application Ownership
- build Community Infrastructure
, without relying on hegemonic Cloud Platforms, no matter their wealth or knowledge levels.
Information Effects enables you to effect changes in the analog world by owning a piece if the digital world.
Cloud Computing has been lim
The opportunity for individuals to change the world at scale has been limited,
Cloud Compute vs Team Compute
With almost everyone on earth being fed a diet of FREE services by Cloud Computing for so many years, it would be difficult to move people away from the Cloud, unless there is something that is BETTER THAN FREE.
The increasing transfer of the world's information assets (and thus power) from so MANY to so FEW is occurring because the Cloud does bring some benefits to the end users in order to suck them in:
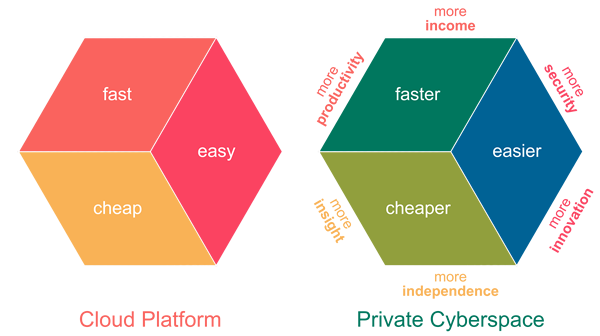
- The Cloud is FAST to join and submit your data into BUT have you tried leaving or taking your data out ? Deleting your data is not so fast ?
- The Cloud is EASY to use if your follow their rules BUT have you had problems with their operation ? Complaining is not so easy ?
- The Cloud is CHEAP when you start BUT what about after you are hooked ? The premium versions are not so cheap ?
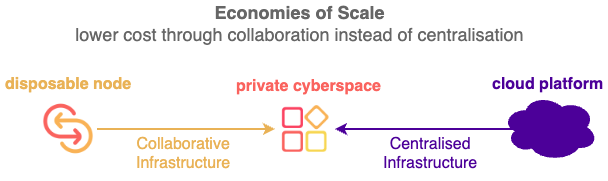
Private Cyberspace does not just deliver compute faster, easier and cheaper than Cloud Platform, it totally transforms how compute is being performed.
Instead of PASSIVELY living in a digital environment determined by the Cloud, now you can ACTIVELY shape your own Private Cyberspace.
- See Clearly - beyond cloud's ranking and recommendation algorithms.
- Think Deeply - without being interrupted by cloud notifications and advertisements.
- Interact Privately - without cloud monitoring your activity and selling your data.
- Act Freely - without following cloud's interests and rules.
Private Cyberspace adds new dimensions to your digital life that are NEVER possible if your live in the Cloud:
- Data that were too private for the cloud can now be analysed by you.
- Automations that were not profitable for the cloud can now be deployed by you.
- Control that was given away to the cloud can now be retained by you.
- Interruptions from cloud notifications and advertisements can now be stopped.
- Views clouded by commercial rankings and recommendations can now be cleared.
- Activities in the interest of users instead of cloud can now be performed.
- Income from processing and data that were captured by the cloud can now be received.
Private Cyberspace has More Than 40 Advantages over Cloud Platforms.
The massive injection of compute power into the whole population improves every aspect of modern life from personal dignity (how you value yourself and how others value you) to national security (wars are won by the industries at the back as much as on the battlefields at the front).
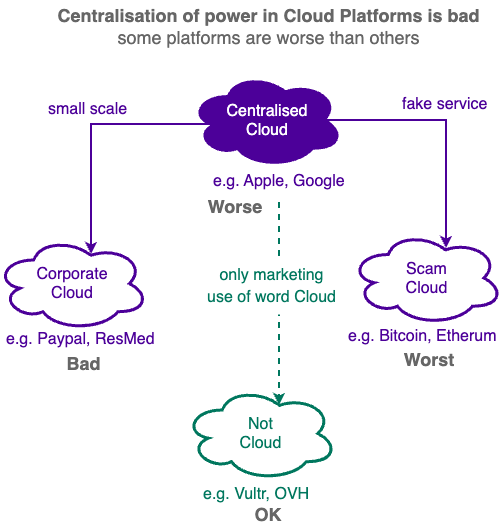
Different Cloud Types
-
Dominant Cloud e.g. Apple, Google, Facebook etc. uses your data and compute resources to control your digital life directly themselves and increasingly letting others control your life as well.
-
Scam Cloud e.g. Bitcoin, Ethereum etc. is a type of Centralised Cloud that pretend to be decentralised when in fact they are not - it still controls you and let others control you like a centralised cloud.
-
Corporate Cloud e.g. Paypal, Resmed etc. is a type of Centralised Cloud that operates at a smaller scale.They are exploitive businesses that share your data or lock up your data, just like bigger centralised clouds.
-
Not Cloud e.g. Vultr, OVH etc. is a business that uses the word "Cloud" in its marketing but it is NOT really a Cloud Platform. It provides non-application specific compute hosting services WITHOUT processing your data for you.
Skill Barrier
No Skill Barrier
Everyone, no matter their skill (from children to retirees), can customise their private cyberspaces by swapping application modules like playing with toy bricks.
How often have you read on the second page of search results?
Control your worldview by deciding what results should be on that first search page.
Since you own the compute in your Private Cyberspace, you can collect, process and distribute data under your own algorithms instead of cloud algorithms.
Discover a new you by storing and analysing ALL your data, not matter how private or trivial, without any cloud or government restrictions e.g privacy laws do not apply.
Personalise your Private Cyberspace by mixing and matching Citizen Modules like toy bricks - NO technical skill required.
Keep swapping modules until you are happy - not everyone knows how to cook but EVERYONE knows what tastes good!